Credit Photo by the Author
Introduction
In an increasingly interconnected digital landscape, cyberattacks from sophisticated state-sponsored groups present a severe threat to organizations worldwide. This reality was recently demonstrated by a significant vulnerability in Microsoft's Azure Active Directory platform that allowed advanced persistent threat (APT) actors to hijack user accounts undetected across numerous high-profile victims.
Storm-0558 Hack
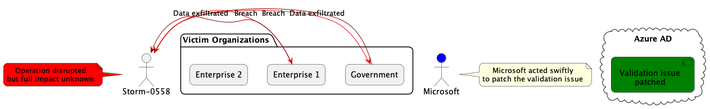
Microsoft disclosed a serious vulnerability last week that allowed a threat group to forge authentication tokens and breach over two dozen organizations via their Microsoft accounts. The China-based hacker group, known as Storm-0558, exploited a validation error in Microsoft's Azure Active Directory (AD) source code to gain unauthorized access to email accounts and exfiltrate sensitive data.

The error enabled the group to use an inactive consumer signing key to forge tokens for both Azure AD enterprise accounts and regular Microsoft accounts. This gave them access to email inboxes and data housed in Microsoft's cloud services.
Microsoft was alerted to the breach after the U.S. State Department noticed suspicious activity related to Exchange Online data. Investigation revealed that Storm-0558 had been actively targeting economic, government, and telecom sectors since at least August 2021.
The group used the forged tokens alongside other tactics like phishing and web shell malware to gain initial access to target networks. Once inside, they were able to operate undetected for over a month, extracting email conversations, attachments, and other confidential information.

While Microsoft has addressed the specific authentication vulnerability exploited in this attack, the full scope of the data breach remains uncertain. Initial assessments indicate approximately 25 organizations globally suffered impacts, including government entities.
This sophisticated cyber espionage operation highlights the growing threat of state-sponsored hackers. As digital networks expand, groups like Storm-0558 are devoting immense resources to stealthily stealing sensitive data for strategic advantage.
Lesson Learns
The case also demonstrates the constant diligence required to keep cloud services secure. Even big tech giants like Microsoft can overlook flaws that advanced persistent threat (APT) groups will exploit. Rapid detection and response are essential to limit damage from such inevitable gaps.
For organizations relying on Microsoft cloud tools, this breach serves as a wakeup call to scrutinize identity and access controls. Multifactor authentication, privilege management, and logging/auditing of account activity are a must to protect against phishing and forged credentials.
As nation-state hacking ramps up, no sector is safe from potential compromise. But with vigilant cybersecurity teams, ongoing staff training, and prompt patching, organizations can minimize both frequency and impact of successful attacks. #cybersecurity #databreach #hacking
Key Takeaways:
🎯 Cloud services contain critical data attractive to hackers - flaws can enable account hijacking
🔑 Enhanced identity/access controls (MFA, privilege management, activity logging) are essential
🧑💻 Staff training critical to avoid phishing, social engineering that grab initial foothold
📵 Rapid detection and response limit damage from inevitable vulnerabilities
🥷 State-sponsored groups devote vast resources to stealthy data theft - constant vigilance needed
🛡️ No organization is immune - prioritize cybersecurity monitoring, hardening, and resilience
🤝 Partnership between security teams and providers strengthens incident response
🔒 Ongoing diligence and prompt patching required to combat persistent hacking threats
How we support organizations with Cybersecurity?
Let our elite team of cyber experts help architect and implement a hardened cloud security posture for your organization leveraging proven methodologies:
- Cloud Infrastructure Audit - We assess your environment identifying crown jewels, vulnerable points, and security gaps.
- Zero Trust Architecture - We design identity and access innovations like MFA, privileged access management, microsegmentation and activity logging.
- 24/7 Threat Monitoring - We establish processes leveraging AI to continuously monitor identity/data access patterns and rapidly flag anomalies.
- Human Defense Training - We build engaging infosec awareness programs, conduct real phishing simulations, and provide response coaching.
- Incident Response Playbooks - We create customized IR blueprints enabling swift containment of cloud attacks.
- Threat Intelligence Integration - We integrate feeds from leading providers and dark web sources into security systems to detect emerging threats.
- Coordinated Response - We facilitate collaboration with Microsoft, AWS cyber teams to coordinate incident response.
- Continuous Optimization - We continuously tune your defenses as the threat landscape evolves.
Our integrated solutions span detection, response, threat hunting - backed by elite talent.
Let's discuss how our consultancy services can transform your cloud security.